PhishFlagger™
The Email Phishing Solution
Latest Phishing News
Subscribe to PhishFlagger News
Tip: To ensure our News mail never go in your junk folder
we recommend you add a new contact as no-reply@phishflaggernews.com
Tip: To ensure our News mail never go in your junk folder we recommend you add a new contact as no-reply@phishflaggernews.com

Q1 Goals to Gaps in Security: The Rise of HR-Themed Phishing

Q1 Goals to Gaps in Security: The Rise of HR-Themed Phishing

Q1 Goals to Gaps in Security: The Rise of HR-Themed Phishing

Q1 Goals to Gaps in Security: The Rise of HR-Themed Phishing

New PoisonSeed Attacking CRM & Bulk Email Providers in Supply Chain Phishing Attack

New PoisonSeed Attacking CRM & Bulk Email Providers in Supply Chain Phishing Attack

New PoisonSeed Attacking CRM & Bulk Email Providers in Supply Chain Phishing Attack

New PoisonSeed Attacking CRM & Bulk Email Providers in Supply Chain Phishing Attack

Hackers Abuse Cloudflare Services for Sophisticated Phishing Attacks

Hackers Abuse Cloudflare Services for Sophisticated Phishing Attacks

Hackers Abuse Cloudflare Services for Sophisticated Phishing Attacks

Hackers Abuse Cloudflare Services for Sophisticated Phishing Attacks

Phishing platform 'Lucid' behind wave of iOS, Android SMS attacks

Phishing platform 'Lucid' behind wave of iOS, Android SMS attacks

Phishing platform 'Lucid' behind wave of iOS, Android SMS attacks

Phishing platform 'Lucid' behind wave of iOS, Android SMS attacks

Top 10 announcements from Black Hat 2024

Top 10 announcements from Black Hat 2024

Top 10 announcements from Black Hat 2024

Top 10 announcements from Black Hat 2024

Phishing Emails Aren't as Obvious Anymore. Here's How to Spot Them

Phishing Emails Aren't as Obvious Anymore. Here's How to Spot Them

Phishing Emails Aren't as Obvious Anymore. Here's How to Spot Them

Phishing Emails Aren't as Obvious Anymore. Here's How to Spot Them

OPP warning Ontarians to be aware of “smishing” fraud

OPP warning Ontarians to be aware of “smishing” fraud

OPP warning Ontarians to be aware of “smishing” fraud

OPP warning Ontarians to be aware of “smishing” fraud

New Data Shows Impact of AI-Powered Phishing on Businesses

New Data Shows Impact of AI-Powered Phishing on Businesses

New Data Shows Impact of AI-Powered Phishing on Businesses

New Data Shows Impact of AI-Powered Phishing on Businesses

⚡ Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More

⚡ Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More

⚡ Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More

⚡ Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More
Hackers Abuse MailChimp Email Marketing Platform via Phishing, and Social Engineering Tactics

Hackers Abuse MailChimp Email Marketing Platform via Phishing, and Social Engineering Tactics

Hackers Abuse MailChimp Email Marketing Platform via Phishing, and Social Engineering Tactics

Hackers Abuse MailChimp Email Marketing Platform via Phishing, and Social Engineering Tactics

ClickFix malware tricks you into infecting your own Windows PC

ClickFix malware tricks you into infecting your own Windows PC

ClickFix malware tricks you into infecting your own Windows PC

ClickFix malware tricks you into infecting your own Windows PC

Phishing Attacks – Anyone Can Get Pwned

Phishing Attacks – Anyone Can Get Pwned

Phishing Attacks – Anyone Can Get Pwned

Phishing Attacks – Anyone Can Get Pwned

New Morphing Meerkat Phishing Kit Mimics 114 Brands Using Victims' DNS Email Records

New Morphing Meerkat Phishing Kit Mimics 114 Brands Using Victims' DNS Email Records

New Morphing Meerkat Phishing Kit Mimics 114 Brands Using Victims' DNS Email Records

New Morphing Meerkat Phishing Kit Mimics 114 Brands Using Victims' DNS Email Records

Why you should never, ever delete your spam email

Why you should never, ever delete your spam email

Why you should never, ever delete your spam email

Why you should never, ever delete your spam email

Microsoft: Exchange Online bug mistakenly quarantines user emails

Microsoft: Exchange Online bug mistakenly quarantines user emails

Microsoft: Exchange Online bug mistakenly quarantines user emails

Microsoft: Exchange Online bug mistakenly quarantines user emails

Securing Your Supply Chain from Phishing Attacks

Securing Your Supply Chain from Phishing Attacks

Securing Your Supply Chain from Phishing Attacks

Securing Your Supply Chain from Phishing Attacks

AI-driven phishing scams exploded last year. The trend continues in 2025

AI-driven phishing scams exploded last year. The trend continues in 2025

AI-driven phishing scams exploded last year. The trend continues in 2025

AI-driven phishing scams exploded last year. The trend continues in 2025

Why So Many Employee Phishing Training Initiatives Fall Short

Why So Many Employee Phishing Training Initiatives Fall Short

Why So Many Employee Phishing Training Initiatives Fall Short

Why So Many Employee Phishing Training Initiatives Fall Short

Why it's time for phishing prevention to move beyond email

Why it's time for phishing prevention to move beyond email

Why it's time for phishing prevention to move beyond email

Why it's time for phishing prevention to move beyond email

Apple’s Passwords app was vulnerable to phishing attacks for nearly three months after launch

Apple’s Passwords app was vulnerable to phishing attacks for nearly three months after launch

Apple’s Passwords app was vulnerable to phishing attacks for nearly three months after launch

Apple’s Passwords app was vulnerable to phishing attacks for nearly three months after launch

Spoofed emails becoming 'increasingly sophisticated': OPP

Spoofed emails becoming 'increasingly sophisticated': OPP

Spoofed emails becoming 'increasingly sophisticated': OPP

Spoofed emails becoming 'increasingly sophisticated': OPP

17% of over 4,500 employees clicked on phishing links during two-week exercise

17% of over 4,500 employees clicked on phishing links during two-week exercise

17% of over 4,500 employees clicked on phishing links during two-week exercise

17% of over 4,500 employees clicked on phishing links during two-week exercise

Hackers Using Advanced MFA-Bypassing Techniques To Gain Access To User Account

Hackers Using Advanced MFA-Bypassing Techniques To Gain Access To User Account

Hackers Using Advanced MFA-Bypassing Techniques To Gain Access To User Account

Hackers Using Advanced MFA-Bypassing Techniques To Gain Access To User Account

Malware's AI time bomb

Malware's AI time bomb

Malware's AI time bomb

Malware's AI time bomb

New Warning As Microsoft 365 Attack Can Bypass Email Security

New Warning As Microsoft 365 Attack Can Bypass Email Security

New Warning As Microsoft 365 Attack Can Bypass Email Security

New Warning As Microsoft 365 Attack Can Bypass Email Security

False confidence leaves businesses at risk of phishing scams

False confidence leaves businesses at risk of phishing scams

False confidence leaves businesses at risk of phishing scams

False confidence leaves businesses at risk of phishing scams

FBI Warns Of Malware Risks In Free Online File Converters: Key Information You Need

FBI Warns Of Malware Risks In Free Online File Converters: Key Information You Need

FBI Warns Of Malware Risks In Free Online File Converters: Key Information You Need

FBI Warns Of Malware Risks In Free Online File Converters: Key Information You Need

PayPal Scam Warning—Dangerous Invoice Bypasses Email Security

PayPal Scam Warning—Dangerous Invoice Bypasses Email Security

PayPal Scam Warning—Dangerous Invoice Bypasses Email Security

PayPal Scam Warning—Dangerous Invoice Bypasses Email Security

Microsoft says malvertising campaign impacted 1 million PCs

Microsoft says malvertising campaign impacted 1 million PCs

Microsoft says malvertising campaign impacted 1 million PCs

Microsoft says malvertising campaign impacted 1 million PCs

2024 phishing trends tell us what to expect in 2025

2024 phishing trends tell us what to expect in 2025

2024 phishing trends tell us what to expect in 2025

2024 phishing trends tell us what to expect in 2025

Google replacing SMS with QR codes for Gmail

Google replacing SMS with QR codes for Gmail

Google replacing SMS with QR codes for Gmail

Google replacing SMS with QR codes for Gmail

YouTube warns of AI-generated video of its CEO used in phishing attacks

YouTube warns of AI-generated video of its CEO used in phishing attacks

YouTube warns of AI-generated video of its CEO used in phishing attacks

YouTube warns of AI-generated video of its CEO used in phishing attacks

This Massive Data Breach Compromised 3.3 Million People's Information

This Massive Data Breach Compromised 3.3 Million People's Information

This Massive Data Breach Compromised 3.3 Million People's Information

This Massive Data Breach Compromised 3.3 Million People's Information

What is vishing? Voice phishing is surging - expert tips on how to spot it and stop it

What is vishing? Voice phishing is surging - expert tips on how to spot it and stop it

What is vishing? Voice phishing is surging - expert tips on how to spot it and stop it

What is vishing? Voice phishing is surging - expert tips on how to spot it and stop it

Roblox Support Team Warns of Password Phishing Scam

Roblox Support Team Warns of Password Phishing Scam

Roblox Support Team Warns of Password Phishing Scam

Roblox Support Team Warns of Password Phishing Scam

‘I did all of my research’: Canadians lose hundreds of thousands in GIC investment scam

‘I did all of my research’: Canadians lose hundreds of thousands in GIC investment scam

‘I did all of my research’: Canadians lose hundreds of thousands in GIC investment scam

‘I did all of my research’: Canadians lose hundreds of thousands in GIC investment scam

Microsoft Outlook email down in global outage: when will it be back online?

Microsoft Outlook email down in global outage: when will it be back online?

Microsoft Outlook email down in global outage: when will it be back online?

Microsoft Outlook email down in global outage: when will it be back online?

The Top 5 Phishing Trends Businesses Need to Know in 2025

The Top 5 Phishing Trends Businesses Need to Know in 2025

The Top 5 Phishing Trends Businesses Need to Know in 2025

The Top 5 Phishing Trends Businesses Need to Know in 2025

New Gmail, Outlook Attacks—Stop Using Your Password And 2FA

New Gmail, Outlook Attacks—Stop Using Your Password And 2FA

New Gmail, Outlook Attacks—Stop Using Your Password And 2FA

New Gmail, Outlook Attacks—Stop Using Your Password And 2FA

Cybercrooks Exploit URL Manipulation in Sophisticated Phishing Scam

Cybercrooks Exploit URL Manipulation in Sophisticated Phishing Scam

Cybercrooks Exploit URL Manipulation in Sophisticated Phishing Scam

Cybercrooks Exploit URL Manipulation in Sophisticated Phishing Scam

This PayPal scam exploits new address feature to send out phishing scam emails

This PayPal scam exploits new address feature to send out phishing scam emails

This PayPal scam exploits new address feature to send out phishing scam emails

This PayPal scam exploits new address feature to send out phishing scam emails

New ChatGPT’s Premium Features Subscription Phishing Attack Steal Logins

New ChatGPT’s Premium Features Subscription Phishing Attack Steal Logins

New ChatGPT’s Premium Features Subscription Phishing Attack Steal Logins

New ChatGPT’s Premium Features Subscription Phishing Attack Steal Logins

Google Confirms Gmail To Ditch SMS Code Authentication

Google Confirms Gmail To Ditch SMS Code Authentication

Google Confirms Gmail To Ditch SMS Code Authentication

Google Confirms Gmail To Ditch SMS Code Authentication

Mobile Phishing Attacks Surge with 16% of Incidents in US

Mobile Phishing Attacks Surge with 16% of Incidents in US

Mobile Phishing Attacks Surge with 16% of Incidents in US

Mobile Phishing Attacks Surge with 16% of Incidents in US

Invisible obfuscation technique used in PAC attack

Invisible obfuscation technique used in PAC attack

Invisible obfuscation technique used in PAC attack

Invisible obfuscation technique used in PAC attack

Phishing attack hides JavaScript using invisible Unicode trick

Phishing attack hides JavaScript using invisible Unicode trick

Phishing attack hides JavaScript using invisible Unicode trick

Phishing attack hides JavaScript using invisible Unicode trick

Warning issued to 2,500,000,000 Gmail users over 'devastating scam' which allows hackers to steal banking and sensitive data

Warning issued to 2,500,000,000 Gmail users over 'devastating scam' which allows hackers to steal banking and sensitive data

Warning issued to 2,500,000,000 Gmail users over 'devastating scam' which allows hackers to steal banking and sensitive data

Warning issued to 2,500,000,000 Gmail users over 'devastating scam' which allows hackers to steal banking and sensitive data

US military and defense contractors hit with Infostealer malware

US military and defense contractors hit with Infostealer malware

US military and defense contractors hit with Infostealer malware

US military and defense contractors hit with Infostealer malware

Gmail And Outlook 2FA Warning—Do Not Use This Sign-In

Gmail And Outlook 2FA Warning—Do Not Use This Sign-In

Gmail And Outlook 2FA Warning—Do Not Use This Sign-In

Gmail And Outlook 2FA Warning—Do Not Use This Sign-In

Astaroth: A New 2FA Phishing Kit Targeting Gmail, Yahoo, AOL, O365, and 3rd-Party Logins

Astaroth: A New 2FA Phishing Kit Targeting Gmail, Yahoo, AOL, O365, and 3rd-Party Logins

Astaroth: A New 2FA Phishing Kit Targeting Gmail, Yahoo, AOL, O365, and 3rd-Party Logins

Astaroth: A New 2FA Phishing Kit Targeting Gmail, Yahoo, AOL, O365, and 3rd-Party Logins

ZeroLogon Ransomware Exploit Active Directory Vulnerability To Gain Domain Controller Access

ZeroLogon Ransomware Exploit Active Directory Vulnerability To Gain Domain Controller Access

ZeroLogon Ransomware Exploit Active Directory Vulnerability To Gain Domain Controller Access

ZeroLogon Ransomware Exploit Active Directory Vulnerability To Gain Domain Controller Access

Google touts 2x phishing, scam protection by enabling Chrome’s Enhanced Safe Browsing

Google touts 2x phishing, scam protection by enabling Chrome’s Enhanced Safe Browsing

Google touts 2x phishing, scam protection by enabling Chrome’s Enhanced Safe Browsing

Google touts 2x phishing, scam protection by enabling Chrome’s Enhanced Safe Browsing

Study: Workplace Phishing Tests Only Have a 2% Success Rate

Study: Workplace Phishing Tests Only Have a 2% Success Rate

Study: Workplace Phishing Tests Only Have a 2% Success Rate

Study: Workplace Phishing Tests Only Have a 2% Success Rate

Phishing Season 2025: The Latest Predictions Unveiled

Phishing Season 2025: The Latest Predictions Unveiled

Phishing Season 2025: The Latest Predictions Unveiled

Phishing Season 2025: The Latest Predictions Unveiled

New Google Chrome Drive-By Hack Attack—Users Must Act Now

New Google Chrome Drive-By Hack Attack—Users Must Act Now

New Google Chrome Drive-By Hack Attack—Users Must Act Now

New Google Chrome Drive-By Hack Attack—Users Must Act Now

SVG files are offering cybercriminals an easy way in with new phishing attacks

SVG files are offering cybercriminals an easy way in with new phishing attacks

SVG files are offering cybercriminals an easy way in with new phishing attacks

SVG files are offering cybercriminals an easy way in with new phishing attacks

Hackers spoof Microsoft ADFS login pages to steal credentials

Hackers spoof Microsoft ADFS login pages to steal credentials

Hackers spoof Microsoft ADFS login pages to steal credentials

Hackers spoof Microsoft ADFS login pages to steal credentials

AI Phishing Revolution: Study Reveals Bots Now Out-Scheme Humans in Cyber Deception

AI Phishing Revolution: Study Reveals Bots Now Out-Scheme Humans in Cyber Deception

AI Phishing Revolution: Study Reveals Bots Now Out-Scheme Humans in Cyber Deception

AI Phishing Revolution: Study Reveals Bots Now Out-Scheme Humans in Cyber Deception

Microsoft authentication system spoofed via phishing attack

Microsoft authentication system spoofed via phishing attack

Microsoft authentication system spoofed via phishing attack

Microsoft authentication system spoofed via phishing attack

Critical RCE bug in Microsoft Outlook now exploited in attacks

Critical RCE bug in Microsoft Outlook now exploited in attacks

Critical RCE bug in Microsoft Outlook now exploited in attacks

Critical RCE bug in Microsoft Outlook now exploited in attacks

Phishing up almost 50 percent since 2021 with AI attacks on the rise

Phishing up almost 50 percent since 2021 with AI attacks on the rise

Phishing up almost 50 percent since 2021 with AI attacks on the rise

Phishing up almost 50 percent since 2021 with AI attacks on the rise

Cyberhaven: A Wake-Up Call for Consent Phishing Risks | Grip

Cyberhaven: A Wake-Up Call for Consent Phishing Risks | Grip

Cyberhaven: A Wake-Up Call for Consent Phishing Risks | Grip

Cyberhaven: A Wake-Up Call for Consent Phishing Risks | Grip

New Email AI Attack Warning As Hackers Create Critical Threat For $5

New Email AI Attack Warning As Hackers Create Critical Threat For $5

New Email AI Attack Warning As Hackers Create Critical Threat For $5

New Email AI Attack Warning As Hackers Create Critical Threat For $5

Google just fixed a zero-day kernel flaw used by hackers and 47 other vulnerabilities — update your Android phone right now

Google just fixed a zero-day kernel flaw used by hackers and 47 other vulnerabilities — update your Android phone right now

Google just fixed a zero-day kernel flaw used by hackers and 47 other vulnerabilities — update your Android phone right now

Google just fixed a zero-day kernel flaw used by hackers and 47 other vulnerabilities — update your Android phone right now

Gmail Security Warning For 2.5 Billion Users—AI Hack Confirmed

Gmail Security Warning For 2.5 Billion Users—AI Hack Confirmed

Gmail Security Warning For 2.5 Billion Users—AI Hack Confirmed

Gmail Security Warning For 2.5 Billion Users—AI Hack Confirmed

Deepfakes, workforce fraud and phishing incidents on the rise across businesses

Deepfakes, workforce fraud and phishing incidents on the rise across businesses

Deepfakes, workforce fraud and phishing incidents on the rise across businesses

Deepfakes, workforce fraud and phishing incidents on the rise across businesses

New iPhone, Android Warning—Do Not Open Any Of These PDFs

New iPhone, Android Warning—Do Not Open Any Of These PDFs

New iPhone, Android Warning—Do Not Open Any Of These PDFs

New iPhone, Android Warning—Do Not Open Any Of These PDFs

Google forced to step up phishing defenses following ‘most sophisticated attack’ it has ever seen

Google forced to step up phishing defenses following ‘most sophisticated attack’ it has ever seen

Google forced to step up phishing defenses following ‘most sophisticated attack’ it has ever seen

Google forced to step up phishing defenses following ‘most sophisticated attack’ it has ever seen

Threat Actors Exploit Government Website Vulnerabilities for Phishing Campaigns

Threat Actors Exploit Government Website Vulnerabilities for Phishing Campaigns

Threat Actors Exploit Government Website Vulnerabilities for Phishing Campaigns

Threat Actors Exploit Government Website Vulnerabilities for Phishing Campaigns

Devil-Traff: A New Bulk SMS Platform Driving Phishing Campaigns

Devil-Traff: A New Bulk SMS Platform Driving Phishing Campaigns

Devil-Traff: A New Bulk SMS Platform Driving Phishing Campaigns

Devil-Traff: A New Bulk SMS Platform Driving Phishing Campaigns

Fake RCMP text messages part of new phishing scam, OPP warns

Fake RCMP text messages part of new phishing scam, OPP warns

Fake RCMP text messages part of new phishing scam, OPP warns

Fake RCMP text messages part of new phishing scam, OPP warns

Eastern Ontario woman out nearly $20,000 in bank scam

Eastern Ontario woman out nearly $20,000 in bank scam

Eastern Ontario woman out nearly $20,000 in bank scam

Eastern Ontario woman out nearly $20,000 in bank scam

Microsoft Teams phishing attack alerts coming to everyone next month

Microsoft Teams phishing attack alerts coming to everyone next month

Microsoft Teams phishing attack alerts coming to everyone next month

Microsoft Teams phishing attack alerts coming to everyone next month

Exploring Q4 2024 Brand Phishing Trends: Microsoft Remains the Top Target as LinkedIn Makes a Comeback

Exploring Q4 2024 Brand Phishing Trends: Microsoft Remains the Top Target as LinkedIn Makes a Comeback

Exploring Q4 2024 Brand Phishing Trends: Microsoft Remains the Top Target as LinkedIn Makes a Comeback

Exploring Q4 2024 Brand Phishing Trends: Microsoft Remains the Top Target as LinkedIn Makes a Comeback

New GhostGPT Chatbot Creates Malware and Phishing Emails

New GhostGPT Chatbot Creates Malware and Phishing Emails

New GhostGPT Chatbot Creates Malware and Phishing Emails

New GhostGPT Chatbot Creates Malware and Phishing Emails

Phishing Campaigns Became a Lot More Sinister in 2024

Phishing Campaigns Became a Lot More Sinister in 2024

Phishing Campaigns Became a Lot More Sinister in 2024

Phishing Campaigns Became a Lot More Sinister in 2024

Tycoon 2FA Phishing Kit Upgraded to Bypass Security Measures

Tycoon 2FA Phishing Kit Upgraded to Bypass Security Measures

Tycoon 2FA Phishing Kit Upgraded to Bypass Security Measures

Tycoon 2FA Phishing Kit Upgraded to Bypass Security Measures

Account Compromise and Phishing Top Healthcare Security Incidents

Account Compromise and Phishing Top Healthcare Security Incidents

Account Compromise and Phishing Top Healthcare Security Incidents

Account Compromise and Phishing Top Healthcare Security Incidents

Investigation into $230K phishing scam results in four more arrests

Investigation into $230K phishing scam results in four more arrests

Investigation into $230K phishing scam results in four more arrests

Investigation into $230K phishing scam results in four more arrests

Ransomware gangs pose as IT support in Microsoft Teams phishing attacks

Ransomware gangs pose as IT support in Microsoft Teams phishing attacks

Ransomware gangs pose as IT support in Microsoft Teams phishing attacks

Ransomware gangs pose as IT support in Microsoft Teams phishing attacks

Phishing Attacks Are the Most Common Smartphone Security Issue for Consumers

Phishing Attacks Are the Most Common Smartphone Security Issue for Consumers

Phishing Attacks Are the Most Common Smartphone Security Issue for Consumers

Phishing Attacks Are the Most Common Smartphone Security Issue for Consumers

New Microsoft 2FA Bypass Attack Warning—Dangerous And Sneaky, Act Now

New Microsoft 2FA Bypass Attack Warning—Dangerous And Sneaky, Act Now

New Microsoft 2FA Bypass Attack Warning—Dangerous And Sneaky, Act Now

New Microsoft 2FA Bypass Attack Warning—Dangerous And Sneaky, Act Now

A Rise in Password Stealers: How to Combat This Dangerous Malware

A Rise in Password Stealers: How to Combat This Dangerous Malware

A Rise in Password Stealers: How to Combat This Dangerous Malware

A Rise in Password Stealers: How to Combat This Dangerous Malware

Google ‘Perpetual Hack’ Attack Steals Passwords And 2FA—Act Now

Google ‘Perpetual Hack’ Attack Steals Passwords And 2FA—Act Now

Google ‘Perpetual Hack’ Attack Steals Passwords And 2FA—Act Now

Google ‘Perpetual Hack’ Attack Steals Passwords And 2FA—Act Now

Hackers leak configs and VPN credentials for 15,000 FortiGate devices

Hackers leak configs and VPN credentials for 15,000 FortiGate devices

Hackers leak configs and VPN credentials for 15,000 FortiGate devices

Hackers leak configs and VPN credentials for 15,000 FortiGate devices

MFA Failures - The Worst is Yet to Come

MFA Failures - The Worst is Yet to Come

MFA Failures - The Worst is Yet to Come

MFA Failures - The Worst is Yet to Come

Critical Microsoft Outlook Vulnerability Rated 9.8/10 Confirmed—Update Now

Critical Microsoft Outlook Vulnerability Rated 9.8/10 Confirmed—Update Now

Critical Microsoft Outlook Vulnerability Rated 9.8/10 Confirmed—Update Now

Critical Microsoft Outlook Vulnerability Rated 9.8/10 Confirmed—Update Now

[HEADS UP] Credential Phishing Increased by 703% in H2 2024

[HEADS UP] Credential Phishing Increased by 703% in H2 2024

[HEADS UP] Credential Phishing Increased by 703% in H2 2024

[HEADS UP] Credential Phishing Increased by 703% in H2 2024

Phishing texts trick Apple iMessage users into disabling protection

Phishing texts trick Apple iMessage users into disabling protection

Phishing texts trick Apple iMessage users into disabling protection

Phishing texts trick Apple iMessage users into disabling protection

Android phone users duped into downloading malware lose at least $625,000 since December

Android phone users duped into downloading malware lose at least $625,000 since December

Android phone users duped into downloading malware lose at least $625,000 since December

Android phone users duped into downloading malware lose at least $625,000 since December

CrowdStrike spoofed in recruitment phishing scam

CrowdStrike spoofed in recruitment phishing scam

CrowdStrike spoofed in recruitment phishing scam

CrowdStrike spoofed in recruitment phishing scam

Biden Cybersecurity Executive Order Nears Publication

Biden Cybersecurity Executive Order Nears Publication

Biden Cybersecurity Executive Order Nears Publication

Biden Cybersecurity Executive Order Nears Publication

Fortinet CISO Details ‘Phish-Free’ Phishing Scheme Using PayPal

Fortinet CISO Details ‘Phish-Free’ Phishing Scheme Using PayPal

Fortinet CISO Details ‘Phish-Free’ Phishing Scheme Using PayPal

Fortinet CISO Details ‘Phish-Free’ Phishing Scheme Using PayPal

Do Not Click—New Gmail, Outlook, Apple Mail Warning For Billions

Do Not Click—New Gmail, Outlook, Apple Mail Warning For Billions

Do Not Click—New Gmail, Outlook, Apple Mail Warning For Billions

Do Not Click—New Gmail, Outlook, Apple Mail Warning For Billions

Crypto Hack Weekly Report: Phishing Attacks Dominate in 2024’s Cybercrime Surge

Crypto Hack Weekly Report: Phishing Attacks Dominate in 2024’s Cybercrime Surge

Crypto Hack Weekly Report: Phishing Attacks Dominate in 2024’s Cybercrime Surge

Crypto Hack Weekly Report: Phishing Attacks Dominate in 2024’s Cybercrime Surge

Users receive at least one advanced phishing link every week

Users receive at least one advanced phishing link every week

Users receive at least one advanced phishing link every week

Users receive at least one advanced phishing link every week

Consent Phishing: The New, Smarter Way to Phish

Consent Phishing: The New, Smarter Way to Phish

Consent Phishing: The New, Smarter Way to Phish

Consent Phishing: The New, Smarter Way to Phish

Phishing scams top crypto security threat of 2024 — CertiK

Phishing scams top crypto security threat of 2024 — CertiK

Phishing scams top crypto security threat of 2024 — CertiK

Phishing scams top crypto security threat of 2024 — CertiK

PLAYFULGHOST Delivered via Phishing and SEO Poisoning in Trojanized VPN Apps

PLAYFULGHOST Delivered via Phishing and SEO Poisoning in Trojanized VPN Apps

PLAYFULGHOST Delivered via Phishing and SEO Poisoning in Trojanized VPN Apps

PLAYFULGHOST Delivered via Phishing and SEO Poisoning in Trojanized VPN Apps

Gmail Security Threat Is Confirmed And Google Won’t Fix It—Here’s Why

Gmail Security Threat Is Confirmed And Google Won’t Fix It—Here’s Why

Gmail Security Threat Is Confirmed And Google Won’t Fix It—Here’s Why

Gmail Security Threat Is Confirmed And Google Won’t Fix It—Here’s Why

AI-generated phishing emails are getting very good at targeting executives

AI-generated phishing emails are getting very good at targeting executives

AI-generated phishing emails are getting very good at targeting executives

AI-generated phishing emails are getting very good at targeting executives

Phishing attacks doubled in 2024, report says

Phishing attacks doubled in 2024, report says

Phishing attacks doubled in 2024, report says

Phishing attacks doubled in 2024, report says

Top 12 ways hackers broke into your systems in 2024

Top 12 ways hackers broke into your systems in 2024

Top 12 ways hackers broke into your systems in 2024

Top 12 ways hackers broke into your systems in 2024

Staying safe from hacking and online scams

Staying safe from hacking and online scams

Staying safe from hacking and online scams

Staying safe from hacking and online scams

What To Do If Your Info Leaks In A Data Breach: A 6-Step Recovery Plan

What To Do If Your Info Leaks In A Data Breach: A 6-Step Recovery Plan

What To Do If Your Info Leaks In A Data Breach: A 6-Step Recovery Plan

What To Do If Your Info Leaks In A Data Breach: A 6-Step Recovery Plan

US Treasury says Chinese hackers stole documents in 'major incident'

US Treasury says Chinese hackers stole documents in 'major incident'

US Treasury says Chinese hackers stole documents in 'major incident'

US Treasury says Chinese hackers stole documents in 'major incident'

Google Chrome 2FA Bypass Attacks Confirmed—Millions Of Users At Risk

Google Chrome 2FA Bypass Attacks Confirmed—Millions Of Users At Risk

Google Chrome 2FA Bypass Attacks Confirmed—Millions Of Users At Risk

Google Chrome 2FA Bypass Attacks Confirmed—Millions Of Users At Risk

WARNING: Multiple Google Chrome Extensions Hacked!

WARNING: Multiple Google Chrome Extensions Hacked!

WARNING: Multiple Google Chrome Extensions Hacked!

WARNING: Multiple Google Chrome Extensions Hacked!

Are You Safe? 15 Ways To Prevent A Hacker Attack Today

Are You Safe? 15 Ways To Prevent A Hacker Attack Today

Are You Safe? 15 Ways To Prevent A Hacker Attack Today

Are You Safe? 15 Ways To Prevent A Hacker Attack Today

Critical Gmail Warning As Real Google Prompts Used In Hack Attacks

Critical Gmail Warning As Real Google Prompts Used In Hack Attacks

Critical Gmail Warning As Real Google Prompts Used In Hack Attacks

Critical Gmail Warning As Real Google Prompts Used In Hack Attacks

Emerging Threats & Vulnerabilities to Prepare for in 2025

Emerging Threats & Vulnerabilities to Prepare for in 2025

Emerging Threats & Vulnerabilities to Prepare for in 2025

Emerging Threats & Vulnerabilities to Prepare for in 2025

iOS devices more exposed to phishing than Android

iOS devices more exposed to phishing than Android

iOS devices more exposed to phishing than Android

iOS devices more exposed to phishing than Android

Top 5 Notable Cyber Attacks in December 2024

Top 5 Notable Cyber Attacks in December 2024

Top 5 Notable Cyber Attacks in December 2024

Top 5 Notable Cyber Attacks in December 2024

FBI Warns Gmail, Outlook, Apple Mail Users—Check 3 Things To Stop Attacks

FBI Warns Gmail, Outlook, Apple Mail Users—Check 3 Things To Stop Attacks

FBI Warns Gmail, Outlook, Apple Mail Users—Check 3 Things To Stop Attacks

FBI Warns Gmail, Outlook, Apple Mail Users—Check 3 Things To Stop Attacks

Credential phishing attacks up over 700 percent

Credential phishing attacks up over 700 percent

Credential phishing attacks up over 700 percent

Credential phishing attacks up over 700 percent

Google’s Gmail Upgrade—Why You Need A New Email Address In 2025

Google’s Gmail Upgrade—Why You Need A New Email Address In 2025

Google’s Gmail Upgrade—Why You Need A New Email Address In 2025

Google’s Gmail Upgrade—Why You Need A New Email Address In 2025

New FlowerStorm Microsoft phishing service fills void left by Rockstar2FA

New FlowerStorm Microsoft phishing service fills void left by Rockstar2FA

New FlowerStorm Microsoft phishing service fills void left by Rockstar2FA

New FlowerStorm Microsoft phishing service fills void left by Rockstar2FA

Could This be true?

Could This be true?

Could This be true?

Could This be true?

Fake Google Calendar invites are the newest phishing trend

Fake Google Calendar invites are the newest phishing trend

Fake Google Calendar invites are the newest phishing trend

Fake Google Calendar invites are the newest phishing trend

Santa's Email Hacked. Christmas Cancelled, How PhishFlagger can Stop Phishing.

Santa's Email Hacked. Christmas Cancelled, How PhishFlagger can Stop Phishing.

Santa's Email Hacked. Christmas Cancelled, How PhishFlagger can Stop Phishing.

Santa's Email Hacked. Christmas Cancelled, How PhishFlagger can Stop Phishing.

Phishing scammers spoof Ledger’s email to send bogus data breach notice

Phishing scammers spoof Ledger’s email to send bogus data breach notice

Phishing scammers spoof Ledger’s email to send bogus data breach notice

Phishing scammers spoof Ledger’s email to send bogus data breach notice

New Email Attack Warning—5 Things To Look Out For

New Email Attack Warning—5 Things To Look Out For

New Email Attack Warning—5 Things To Look Out For

New Email Attack Warning—5 Things To Look Out For

Spain busts voice phishing ring for defrauding 10,000 bank customers

Spain busts voice phishing ring for defrauding 10,000 bank customers

Spain busts voice phishing ring for defrauding 10,000 bank customers

Spain busts voice phishing ring for defrauding 10,000 bank customers

Ho-Ho-Hold the Scams: Safeguarding Your Employees Against Holiday Phishing Scams

Ho-Ho-Hold the Scams: Safeguarding Your Employees Against Holiday Phishing Scams

Ho-Ho-Hold the Scams: Safeguarding Your Employees Against Holiday Phishing Scams

Ho-Ho-Hold the Scams: Safeguarding Your Employees Against Holiday Phishing Scams

This phishing scam uses text messages pretending to be USPS with a delivery

This phishing scam uses text messages pretending to be USPS with a delivery

This phishing scam uses text messages pretending to be USPS with a delivery

This phishing scam uses text messages pretending to be USPS with a delivery

KnowBe4 Releases the Latest Phishing Trends in Q3 2024 Phishing Report

KnowBe4 Releases the Latest Phishing Trends in Q3 2024 Phishing Report

KnowBe4 Releases the Latest Phishing Trends in Q3 2024 Phishing Report

KnowBe4 Releases the Latest Phishing Trends in Q3 2024 Phishing Report
Chairwoman Rosenworcel Announces Agency Action to Require Telecom Carriers to Secure Their Networks

Chairwoman Rosenworcel Announces Agency Action to Require Telecom Carriers to Secure Their Networks

Chairwoman Rosenworcel Announces Agency Action to Require Telecom Carriers to Secure Their Networks

Chairwoman Rosenworcel Announces Agency Action to Require Telecom Carriers to Secure Their Networks

FCC to telecoms: Secure your networks from hacks like China’s Salt Typhoon

FCC to telecoms: Secure your networks from hacks like China’s Salt Typhoon

FCC to telecoms: Secure your networks from hacks like China’s Salt Typhoon

FCC to telecoms: Secure your networks from hacks like China’s Salt Typhoon

Holiday Season Cyber Threats (Part 1): Phishing, Fake Shops and Bogus Bookings

Holiday Season Cyber Threats (Part 1): Phishing, Fake Shops and Bogus Bookings

Holiday Season Cyber Threats (Part 1): Phishing, Fake Shops and Bogus Bookings

Holiday Season Cyber Threats (Part 1): Phishing, Fake Shops and Bogus Bookings

Brain Cipher Ransomware: In-Depth Analysis, Detection, and Mitigation

Brain Cipher Ransomware: In-Depth Analysis, Detection, and Mitigation

Brain Cipher Ransomware: In-Depth Analysis, Detection, and Mitigation

Brain Cipher Ransomware: In-Depth Analysis, Detection, and Mitigation

Deloitte Allegedly Hacked By Notorious Ransomware Group

Deloitte Allegedly Hacked By Notorious Ransomware Group

Deloitte Allegedly Hacked By Notorious Ransomware Group

Deloitte Allegedly Hacked By Notorious Ransomware Group

Kimsuky Group Adopts New Phishing Tactics to Target Victims

Kimsuky Group Adopts New Phishing Tactics to Target Victims

Kimsuky Group Adopts New Phishing Tactics to Target Victims

Kimsuky Group Adopts New Phishing Tactics to Target Victims

AV-Comparatives Announces 2024 Phishing Test Results: Avast and McAfee Excel in Yearly Assessment

AV-Comparatives Announces 2024 Phishing Test Results: Avast and McAfee Excel in Yearly Assessment

AV-Comparatives Announces 2024 Phishing Test Results: Avast and McAfee Excel in Yearly Assessment

AV-Comparatives Announces 2024 Phishing Test Results: Avast and McAfee Excel in Yearly Assessment

Microsoft Unveils Windows Resiliency Initiative To Prevent Phishing Attacks

Microsoft Unveils Windows Resiliency Initiative To Prevent Phishing Attacks

Microsoft Unveils Windows Resiliency Initiative To Prevent Phishing Attacks

Microsoft Unveils Windows Resiliency Initiative To Prevent Phishing Attacks

Potential Spike in Crypto Phishing Scams Predicted Amid Holiday Season, Experts Advise Caution

Potential Spike in Crypto Phishing Scams Predicted Amid Holiday Season, Experts Advise Caution

Potential Spike in Crypto Phishing Scams Predicted Amid Holiday Season, Experts Advise Caution

Potential Spike in Crypto Phishing Scams Predicted Amid Holiday Season, Experts Advise Caution

‘Exponential’ rise in scams amid Canada Post strike, holiday shopping

‘Exponential’ rise in scams amid Canada Post strike, holiday shopping

‘Exponential’ rise in scams amid Canada Post strike, holiday shopping

‘Exponential’ rise in scams amid Canada Post strike, holiday shopping

North Korean Hacking Group Launches Undetected Malwareless URL Phishing Attacks

North Korean Hacking Group Launches Undetected Malwareless URL Phishing Attacks

North Korean Hacking Group Launches Undetected Malwareless URL Phishing Attacks

North Korean Hacking Group Launches Undetected Malwareless URL Phishing Attacks

Novel phishing campaign uses corrupted Word documents to evade security

Novel phishing campaign uses corrupted Word documents to evade security

Novel phishing campaign uses corrupted Word documents to evade security

Novel phishing campaign uses corrupted Word documents to evade security

Phishing Attacks Dominate Threat Landscape in Q3 2024

Phishing Attacks Dominate Threat Landscape in Q3 2024

Phishing Attacks Dominate Threat Landscape in Q3 2024

Phishing Attacks Dominate Threat Landscape in Q3 2024

Phishing Prevention Framework Reduces Incidents by Half

Phishing Prevention Framework Reduces Incidents by Half

Phishing Prevention Framework Reduces Incidents by Half

Phishing Prevention Framework Reduces Incidents by Half

New Rockstar 2FA phishing service targets Microsoft 365 accounts

New Rockstar 2FA phishing service targets Microsoft 365 accounts

New Rockstar 2FA phishing service targets Microsoft 365 accounts

New Rockstar 2FA phishing service targets Microsoft 365 accounts

Rising Abuse of URL Rewriting in Phishing Attacks: A Growing Threat

Rising Abuse of URL Rewriting in Phishing Attacks: A Growing Threat

Rising Abuse of URL Rewriting in Phishing Attacks: A Growing Threat

Rising Abuse of URL Rewriting in Phishing Attacks: A Growing Threat

Phishing campaigns target Black Friday shoppers. Here's how to spot them.

Phishing campaigns target Black Friday shoppers. Here's how to spot them.

Phishing campaigns target Black Friday shoppers. Here's how to spot them.

Phishing campaigns target Black Friday shoppers. Here's how to spot them.

Keep Your Eye Out for Signs of This Apple ID Phishing Scam

Keep Your Eye Out for Signs of This Apple ID Phishing Scam

Keep Your Eye Out for Signs of This Apple ID Phishing Scam

Keep Your Eye Out for Signs of This Apple ID Phishing Scam

The phishing threat landscape evolves

The phishing threat landscape evolves

The phishing threat landscape evolves

The phishing threat landscape evolves

Cybercriminals launch over 38m phishing attacks in 2024

Cybercriminals launch over 38m phishing attacks in 2024

Cybercriminals launch over 38m phishing attacks in 2024

Cybercriminals launch over 38m phishing attacks in 2024
Hackers Abuse URL Rewriting In Sophisticated Phishing Attack

Hackers Abuse URL Rewriting In Sophisticated Phishing Attack

Hackers Abuse URL Rewriting In Sophisticated Phishing Attack

Hackers Abuse URL Rewriting In Sophisticated Phishing Attack

Cybercriminals target shoppers with 38 million phishing scams

Cybercriminals target shoppers with 38 million phishing scams

Cybercriminals target shoppers with 38 million phishing scams

Cybercriminals target shoppers with 38 million phishing scams
Voice Phishing Attacks: How to Prevent and Respond to Them

Voice Phishing Attacks: How to Prevent and Respond to Them

Voice Phishing Attacks: How to Prevent and Respond to Them

Voice Phishing Attacks: How to Prevent and Respond to Them
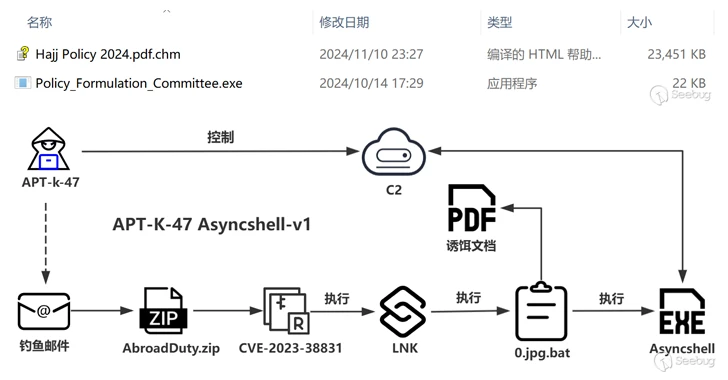
APT-K-47 Uses Hajj-Themed Lures to Deliver Advanced Asyncshell Malware

APT-K-47 Uses Hajj-Themed Lures to Deliver Advanced Asyncshell Malware

APT-K-47 Uses Hajj-Themed Lures to Deliver Advanced Asyncshell Malware

APT-K-47 Uses Hajj-Themed Lures to Deliver Advanced Asyncshell Malware

Phishing-Resistant Multi-Factor Authentication (MFA) Success Story: USDA’s Fast IDentity Online (FIDO) Implementation

Phishing-Resistant Multi-Factor Authentication (MFA) Success Story: USDA’s Fast IDentity Online (FIDO) Implementation

Phishing-Resistant Multi-Factor Authentication (MFA) Success Story: USDA’s Fast IDentity Online (FIDO) Implementation

Phishing-Resistant Multi-Factor Authentication (MFA) Success Story: USDA’s Fast IDentity Online (FIDO) Implementation

Don’t get caught in the 'Apple ID suspended' phishing scam

Don’t get caught in the 'Apple ID suspended' phishing scam

Don’t get caught in the 'Apple ID suspended' phishing scam

Don’t get caught in the 'Apple ID suspended' phishing scam

Email Phishing and DMARC Statistics

Email Phishing and DMARC Statistics

Email Phishing and DMARC Statistics

Email Phishing and DMARC Statistics

A Step by Step Guide to SS7 Attacks

A Step by Step Guide to SS7 Attacks

A Step by Step Guide to SS7 Attacks

A Step by Step Guide to SS7 Attacks

Experts Uncover 70,000 Hijacked Domains in Widespread 'Sitting Ducks' Attack Scheme

Experts Uncover 70,000 Hijacked Domains in Widespread 'Sitting Ducks' Attack Scheme

Experts Uncover 70,000 Hijacked Domains in Widespread 'Sitting Ducks' Attack Scheme

Experts Uncover 70,000 Hijacked Domains in Widespread 'Sitting Ducks' Attack Scheme

Experts warn businesses of escalating cyber security threats

Experts warn businesses of escalating cyber security threats

Experts warn businesses of escalating cyber security threats

Experts warn businesses of escalating cyber security threats

Targeting the Cybercrime Supply Chain

Targeting the Cybercrime Supply Chain

Targeting the Cybercrime Supply Chain

Targeting the Cybercrime Supply Chain

Cyber threats in Pakistan’s finance sector surge by 114pc in 2024: report

Cyber threats in Pakistan’s finance sector surge by 114pc in 2024: report

Cyber threats in Pakistan’s finance sector surge by 114pc in 2024: report

Cyber threats in Pakistan’s finance sector surge by 114pc in 2024: report

US charges 5 in $11M crypto hacking scheme linked to ‘Scattered Spider’

US charges 5 in $11M crypto hacking scheme linked to ‘Scattered Spider’

US charges 5 in $11M crypto hacking scheme linked to ‘Scattered Spider’

US charges 5 in $11M crypto hacking scheme linked to ‘Scattered Spider’

5 Defendants Charged Federally with Running Scheme that Targeted Victim Companies via Phishing Text Messages

5 Defendants Charged Federally with Running Scheme that Targeted Victim Companies via Phishing Text Messages

5 Defendants Charged Federally with Running Scheme that Targeted Victim Companies via Phishing Text Messages

5 Defendants Charged Federally with Running Scheme that Targeted Victim Companies via Phishing Text Messages

You're Not Imagining It: Phishing Attacks Are Rampant

You're Not Imagining It: Phishing Attacks Are Rampant

You're Not Imagining It: Phishing Attacks Are Rampant

You're Not Imagining It: Phishing Attacks Are Rampant

Phishing emails increasingly use SVG attachments to evade detection

Phishing emails increasingly use SVG attachments to evade detection

Phishing emails increasingly use SVG attachments to evade detection

Phishing emails increasingly use SVG attachments to evade detection

GoIssue – The Tool Behind Recent GitHub Phishing Attacks

GoIssue – The Tool Behind Recent GitHub Phishing Attacks

GoIssue – The Tool Behind Recent GitHub Phishing Attacks

GoIssue – The Tool Behind Recent GitHub Phishing Attacks

Don’t Hold Down The Ctrl Key—New Warning As Cyber Attacks Confirmed

Don’t Hold Down The Ctrl Key—New Warning As Cyber Attacks Confirmed

Don’t Hold Down The Ctrl Key—New Warning As Cyber Attacks Confirmed

Don’t Hold Down The Ctrl Key—New Warning As Cyber Attacks Confirmed

How Digital Fraud Has Evolved: Key Takeaways for CISOs

How Digital Fraud Has Evolved: Key Takeaways for CISOs

How Digital Fraud Has Evolved: Key Takeaways for CISOs

How Digital Fraud Has Evolved: Key Takeaways for CISOs

Yubico Unveils Yubico Enrollment Suite To Fast-Track Phishing-Resistance At Scale

Yubico Unveils Yubico Enrollment Suite To Fast-Track Phishing-Resistance At Scale

Yubico Unveils Yubico Enrollment Suite To Fast-Track Phishing-Resistance At Scale

Yubico Unveils Yubico Enrollment Suite To Fast-Track Phishing-Resistance At Scale

Gone phishing: The need to create a culture of cybersecurity awareness

Gone phishing: The need to create a culture of cybersecurity awareness

Gone phishing: The need to create a culture of cybersecurity awareness

Gone phishing: The need to create a culture of cybersecurity awareness

GigaChad Investor Loses $6 Million in Phishing Attack Involving Fake Zoom Link

GigaChad Investor Loses $6 Million in Phishing Attack Involving Fake Zoom Link

GigaChad Investor Loses $6 Million in Phishing Attack Involving Fake Zoom Link

GigaChad Investor Loses $6 Million in Phishing Attack Involving Fake Zoom Link

GoIssue phishing tool targets GitHub developer credentials

GoIssue phishing tool targets GitHub developer credentials

GoIssue phishing tool targets GitHub developer credentials

GoIssue phishing tool targets GitHub developer credentials
The rise of phishing-resistant MFA and what it means for a passwordless future

The rise of phishing-resistant MFA and what it means for a passwordless future

The rise of phishing-resistant MFA and what it means for a passwordless future

The rise of phishing-resistant MFA and what it means for a passwordless future

Hackers Leveraging Microsoft Visio Files & SharePoint For Two-Step Phishing Attack

Hackers Leveraging Microsoft Visio Files & SharePoint For Two-Step Phishing Attack

Hackers Leveraging Microsoft Visio Files & SharePoint For Two-Step Phishing Attack

Hackers Leveraging Microsoft Visio Files & SharePoint For Two-Step Phishing Attack

This new phishing strategy utilizes GitHub comments to distribute malware

This new phishing strategy utilizes GitHub comments to distribute malware

This new phishing strategy utilizes GitHub comments to distribute malware

This new phishing strategy utilizes GitHub comments to distribute malware

Gmail Users Beware—Link Hovering Attacks On The Up

Gmail Users Beware—Link Hovering Attacks On The Up

Gmail Users Beware—Link Hovering Attacks On The Up

Gmail Users Beware—Link Hovering Attacks On The Up

New Chrome, Safari, Edge, Firefox Warning—Do Not Use These Websites

New Chrome, Safari, Edge, Firefox Warning—Do Not Use These Websites

New Chrome, Safari, Edge, Firefox Warning—Do Not Use These Websites

New Chrome, Safari, Edge, Firefox Warning—Do Not Use These Websites

FBI Warns Gmail, Outlook Users Of $100 Government Emergency Data Email Hack

FBI Warns Gmail, Outlook Users Of $100 Government Emergency Data Email Hack

FBI Warns Gmail, Outlook Users Of $100 Government Emergency Data Email Hack

FBI Warns Gmail, Outlook Users Of $100 Government Emergency Data Email Hack

Windows infected with backdoored Linux VMs in new phishing attacks

Windows infected with backdoored Linux VMs in new phishing attacks

Windows infected with backdoored Linux VMs in new phishing attacks

Windows infected with backdoored Linux VMs in new phishing attacks

New Microsoft Windows Password Warning—Stop Doing This Now, U.S. Government Says

New Microsoft Windows Password Warning—Stop Doing This Now, U.S. Government Says

New Microsoft Windows Password Warning—Stop Doing This Now, U.S. Government Says

New Microsoft Windows Password Warning—Stop Doing This Now, U.S. Government Says

Elections Nova Scotia warns of phishing scam trying to collect personal information

Elections Nova Scotia warns of phishing scam trying to collect personal information

Elections Nova Scotia warns of phishing scam trying to collect personal information

Elections Nova Scotia warns of phishing scam trying to collect personal information

Trust and risk in the AI era

Trust and risk in the AI era

Trust and risk in the AI era

Trust and risk in the AI era

Email Phishing Playbook for Efficient Phishing Handling: Attack That’s Hard to Ignore

Email Phishing Playbook for Efficient Phishing Handling: Attack That’s Hard to Ignore

Email Phishing Playbook for Efficient Phishing Handling: Attack That’s Hard to Ignore

Email Phishing Playbook for Efficient Phishing Handling: Attack That’s Hard to Ignore

FBI Warns Gmail, Outlook, AOL, Yahoo Users—Hackers Gain Access To Accounts

FBI Warns Gmail, Outlook, AOL, Yahoo Users—Hackers Gain Access To Accounts

FBI Warns Gmail, Outlook, AOL, Yahoo Users—Hackers Gain Access To Accounts

FBI Warns Gmail, Outlook, AOL, Yahoo Users—Hackers Gain Access To Accounts

New Windows Warning As Hacker Breaks Google Chrome 2FA Security Encryption

New Windows Warning As Hacker Breaks Google Chrome 2FA Security Encryption

New Windows Warning As Hacker Breaks Google Chrome 2FA Security Encryption

New Windows Warning As Hacker Breaks Google Chrome 2FA Security Encryption

2,500,000,000 Gmail Users Targeted in Viral AI Hack That Tricks Users Into Accepting ‘Security Alert’: Report

2,500,000,000 Gmail Users Targeted in Viral AI Hack That Tricks Users Into Accepting ‘Security Alert’: Report

2,500,000,000 Gmail Users Targeted in Viral AI Hack That Tricks Users Into Accepting ‘Security Alert’: Report

2,500,000,000 Gmail Users Targeted in Viral AI Hack That Tricks Users Into Accepting ‘Security Alert’: Report

CISA and FBI Release Product Security Bad Practices for Public Comment

CISA and FBI Release Product Security Bad Practices for Public Comment

CISA and FBI Release Product Security Bad Practices for Public Comment

CISA and FBI Release Product Security Bad Practices for Public Comment

Joint Statement by FBI and CISA on PRC Activity Targeting Telecommunications

Joint Statement by FBI and CISA on PRC Activity Targeting Telecommunications

Joint Statement by FBI and CISA on PRC Activity Targeting Telecommunications

Joint Statement by FBI and CISA on PRC Activity Targeting Telecommunications

CISA Releases Its First Ever International Strategic Plan

CISA Releases Its First Ever International Strategic Plan

CISA Releases Its First Ever International Strategic Plan

CISA Releases Its First Ever International Strategic Plan

Phishing Attacks Are Evolving. Here’s How to Resist Them.

Phishing Attacks Are Evolving. Here’s How to Resist Them.

Phishing Attacks Are Evolving. Here’s How to Resist Them.

Phishing Attacks Are Evolving. Here’s How to Resist Them.

Nintendo Warns Users on Phishing Attack Mimics Company’s Email

Nintendo Warns Users on Phishing Attack Mimics Company’s Email

Nintendo Warns Users on Phishing Attack Mimics Company’s Email

Nintendo Warns Users on Phishing Attack Mimics Company’s Email

AWS breaks up massive Russian phishing operation

AWS breaks up massive Russian phishing operation

AWS breaks up massive Russian phishing operation

AWS breaks up massive Russian phishing operation

New Phishing Schemes To Watch Out For

New Phishing Schemes To Watch Out For

New Phishing Schemes To Watch Out For

New Phishing Schemes To Watch Out For

AI and deepfakes fuel phishing scams, making detection harder

AI and deepfakes fuel phishing scams, making detection harder

AI and deepfakes fuel phishing scams, making detection harder

AI and deepfakes fuel phishing scams, making detection harder

Beyond Business Email Compromise: Multi-Channel Phishing Is Here To Stay

Beyond Business Email Compromise: Multi-Channel Phishing Is Here To Stay

Beyond Business Email Compromise: Multi-Channel Phishing Is Here To Stay

Beyond Business Email Compromise: Multi-Channel Phishing Is Here To Stay

UK CYBERSECURITY REPORT 2024

UK CYBERSECURITY REPORT 2024

UK CYBERSECURITY REPORT 2024

UK CYBERSECURITY REPORT 2024
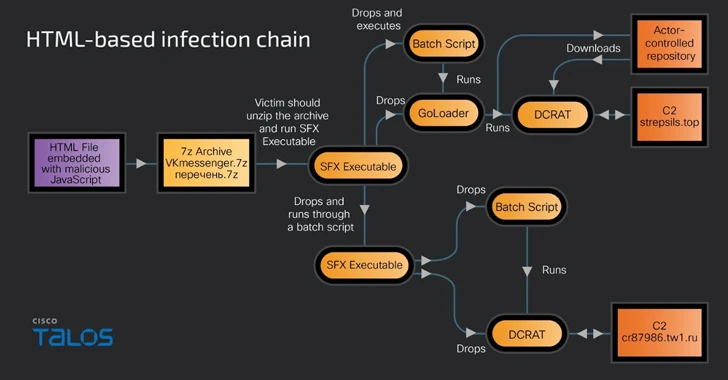
Gophish Framework Used in Phishing Campaigns to Deploy Remote Access Trojans

Gophish Framework Used in Phishing Campaigns to Deploy Remote Access Trojans

Gophish Framework Used in Phishing Campaigns to Deploy Remote Access Trojans

Gophish Framework Used in Phishing Campaigns to Deploy Remote Access Trojans

Callback Phishing Attacks Using Google Groups To Steal Login Details

Callback Phishing Attacks Using Google Groups To Steal Login Details

Callback Phishing Attacks Using Google Groups To Steal Login Details

Callback Phishing Attacks Using Google Groups To Steal Login Details

Gmail Security—Viral AI Hack Poses Critical Question For 2.5 Billion Users

Gmail Security—Viral AI Hack Poses Critical Question For 2.5 Billion Users

Gmail Security—Viral AI Hack Poses Critical Question For 2.5 Billion Users

Gmail Security—Viral AI Hack Poses Critical Question For 2.5 Billion Users

A Look at the Social Engineering Element of Spear Phishing Attacks

A Look at the Social Engineering Element of Spear Phishing Attacks

A Look at the Social Engineering Element of Spear Phishing Attacks

A Look at the Social Engineering Element of Spear Phishing Attacks

Anti-Bot Services Help Cybercrooks Bypass Google 'Red Page'

Anti-Bot Services Help Cybercrooks Bypass Google 'Red Page'

Anti-Bot Services Help Cybercrooks Bypass Google 'Red Page'

Anti-Bot Services Help Cybercrooks Bypass Google 'Red Page'

Phishing scams and malicious domains take center stage as the US election approaches

Phishing scams and malicious domains take center stage as the US election approaches

Phishing scams and malicious domains take center stage as the US election approaches

Phishing scams and malicious domains take center stage as the US election approaches

Wiper malware deployed against Israel via spoofed ESET emails

Wiper malware deployed against Israel via spoofed ESET emails

Wiper malware deployed against Israel via spoofed ESET emails

Wiper malware deployed against Israel via spoofed ESET emails
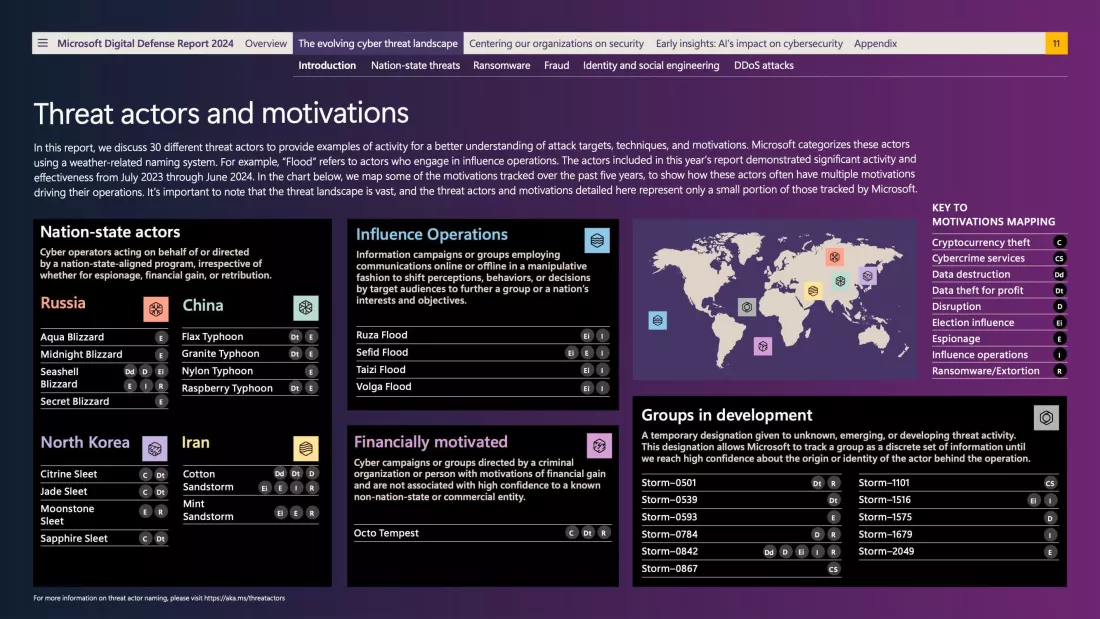
Microsoft warns of 600 million daily cyberattacks and advanced tactics by nation-state actors

Microsoft warns of 600 million daily cyberattacks and advanced tactics by nation-state actors

Microsoft warns of 600 million daily cyberattacks and advanced tactics by nation-state actors

Microsoft warns of 600 million daily cyberattacks and advanced tactics by nation-state actors
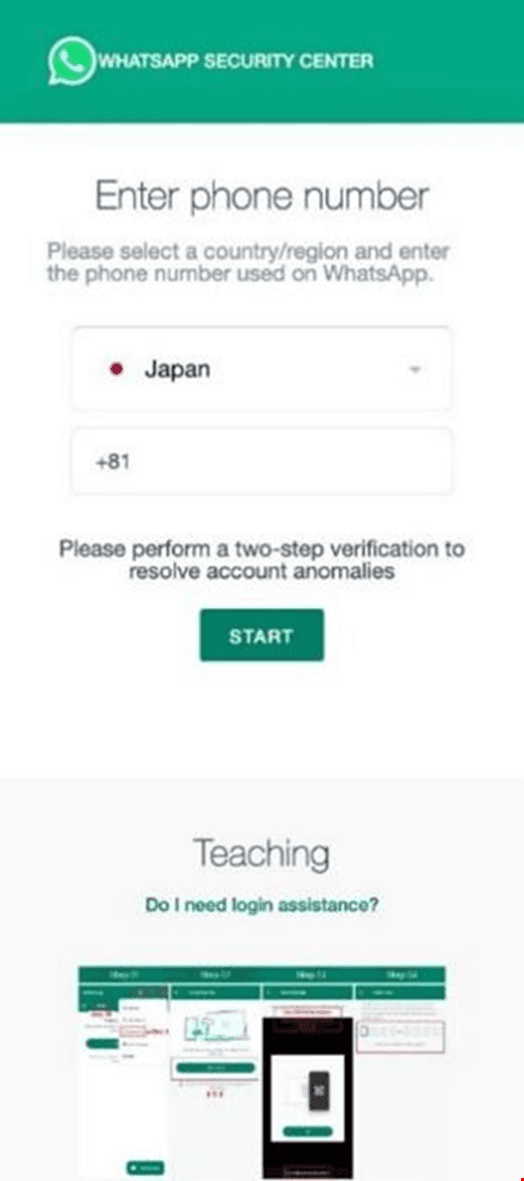
Microsoft Named Most Imitated Brand in Phishing Attacks

Microsoft Named Most Imitated Brand in Phishing Attacks

Microsoft Named Most Imitated Brand in Phishing Attacks

Microsoft Named Most Imitated Brand in Phishing Attacks

Human error is the weakest link in the cyber security chain. Here are 3 ways to fix it

Human error is the weakest link in the cyber security chain. Here are 3 ways to fix it

Human error is the weakest link in the cyber security chain. Here are 3 ways to fix it

Human error is the weakest link in the cyber security chain. Here are 3 ways to fix it

5 online safety tips that can keep you safe from most scams and phishing attempts

5 online safety tips that can keep you safe from most scams and phishing attempts

5 online safety tips that can keep you safe from most scams and phishing attempts

5 online safety tips that can keep you safe from most scams and phishing attempts

Angel Drainer Acquires Rival Crypto Phishing Service Inferno

Angel Drainer Acquires Rival Crypto Phishing Service Inferno

Angel Drainer Acquires Rival Crypto Phishing Service Inferno

Angel Drainer Acquires Rival Crypto Phishing Service Inferno

HIDDEN CON I was SCAMMED out of £100s by hidden sticker parking fee con – know the signs so you don’t fall for it too

HIDDEN CON I was SCAMMED out of £100s by hidden sticker parking fee con – know the signs so you don’t fall for it too

HIDDEN CON I was SCAMMED out of £100s by hidden sticker parking fee con – know the signs so you don’t fall for it too

HIDDEN CON I was SCAMMED out of £100s by hidden sticker parking fee con – know the signs so you don’t fall for it too

Phishing Attack Impacts Over 92,000 Transak Users

Phishing Attack Impacts Over 92,000 Transak Users

Phishing Attack Impacts Over 92,000 Transak Users

Phishing Attack Impacts Over 92,000 Transak Users

Implementing Phishing-Resistant MFA

Implementing Phishing-Resistant MFA

Implementing Phishing-Resistant MFA

Implementing Phishing-Resistant MFA

New Gmail Security Alert For 2.5 Billion Users As AI Hack Confirmed

New Gmail Security Alert For 2.5 Billion Users As AI Hack Confirmed

New Gmail Security Alert For 2.5 Billion Users As AI Hack Confirmed

New Gmail Security Alert For 2.5 Billion Users As AI Hack Confirmed

New Report Reveals a Rise in Phishing Attacks, as Commodity Campaigns, and Impersonation Attacks Escalate

New Report Reveals a Rise in Phishing Attacks, as Commodity Campaigns, and Impersonation Attacks Escalate

New Report Reveals a Rise in Phishing Attacks, as Commodity Campaigns, and Impersonation Attacks Escalate

New Report Reveals a Rise in Phishing Attacks, as Commodity Campaigns, and Impersonation Attacks Escalate

Microsoft Digital Defense Report 2024 Reveals It Defends Against 600M+ Cyber Attacks Daily

Microsoft Digital Defense Report 2024 Reveals It Defends Against 600M+ Cyber Attacks Daily

Microsoft Digital Defense Report 2024 Reveals It Defends Against 600M+ Cyber Attacks Daily

Microsoft Digital Defense Report 2024 Reveals It Defends Against 600M+ Cyber Attacks Daily

Phishing-Resistant MFA For Crypto Asset Security

Phishing-Resistant MFA For Crypto Asset Security

Phishing-Resistant MFA For Crypto Asset Security

Phishing-Resistant MFA For Crypto Asset Security

Arctic Wolf 2024 Human Risk Behavior Snapshot Reveals Nearly Two-Thirds of Security and IT Leaders Have Fallen for Phishing Attacks

Arctic Wolf 2024 Human Risk Behavior Snapshot Reveals Nearly Two-Thirds of Security and IT Leaders Have Fallen for Phishing Attacks

Arctic Wolf 2024 Human Risk Behavior Snapshot Reveals Nearly Two-Thirds of Security and IT Leaders Have Fallen for Phishing Attacks

Arctic Wolf 2024 Human Risk Behavior Snapshot Reveals Nearly Two-Thirds of Security and IT Leaders Have Fallen for Phishing Attacks

Criipto CEO’s phishing tales make for a wild ride at Authenticate 2024

Criipto CEO’s phishing tales make for a wild ride at Authenticate 2024

Criipto CEO’s phishing tales make for a wild ride at Authenticate 2024

Criipto CEO’s phishing tales make for a wild ride at Authenticate 2024

Coffee Lovers Warned of New Starbucks Phishing Scam

Coffee Lovers Warned of New Starbucks Phishing Scam

Coffee Lovers Warned of New Starbucks Phishing Scam

Coffee Lovers Warned of New Starbucks Phishing Scam

Attackers are using QR codes sneakily crafted in ASCII and blob URLs in phishing emails

Attackers are using QR codes sneakily crafted in ASCII and blob URLs in phishing emails

Attackers are using QR codes sneakily crafted in ASCII and blob URLs in phishing emails

Attackers are using QR codes sneakily crafted in ASCII and blob URLs in phishing emails

Fox News AI Newsletter: AI-powered scam targets Gmail users

Fox News AI Newsletter: AI-powered scam targets Gmail users

Fox News AI Newsletter: AI-powered scam targets Gmail users

Fox News AI Newsletter: AI-powered scam targets Gmail users

Phishing Protection Market Size Worth $5.94 Billion, Globally, by 2031 - Exclusive Report by The Insight Partners

Phishing Protection Market Size Worth $5.94 Billion, Globally, by 2031 - Exclusive Report by The Insight Partners

Phishing Protection Market Size Worth $5.94 Billion, Globally, by 2031 - Exclusive Report by The Insight Partners

Phishing Protection Market Size Worth $5.94 Billion, Globally, by 2031 - Exclusive Report by The Insight Partners

RTF-based phishing attacks explode as malicious emails and attachments look more trustworthy than ever

RTF-based phishing attacks explode as malicious emails and attachments look more trustworthy than ever

RTF-based phishing attacks explode as malicious emails and attachments look more trustworthy than ever

RTF-based phishing attacks explode as malicious emails and attachments look more trustworthy than ever

Calgary Public Library cybersecurity breach a concern for customers as branches stay closed

Calgary Public Library cybersecurity breach a concern for customers as branches stay closed

Calgary Public Library cybersecurity breach a concern for customers as branches stay closed

Calgary Public Library cybersecurity breach a concern for customers as branches stay closed

OpenAI Confirms State Sponsored Threat Actors Using ChatGPT For Cyber Attacks

OpenAI Confirms State Sponsored Threat Actors Using ChatGPT For Cyber Attacks

OpenAI Confirms State Sponsored Threat Actors Using ChatGPT For Cyber Attacks

OpenAI Confirms State Sponsored Threat Actors Using ChatGPT For Cyber Attacks

On Your Side: No, your Sam’s Club membership did not expire; don’t click email scam

On Your Side: No, your Sam’s Club membership did not expire; don’t click email scam

On Your Side: No, your Sam’s Club membership did not expire; don’t click email scam

On Your Side: No, your Sam’s Club membership did not expire; don’t click email scam

U.S. and Microsoft Seize 107 Russian Domains in Major Cyber Fraud Crackdown

U.S. and Microsoft Seize 107 Russian Domains in Major Cyber Fraud Crackdown

U.S. and Microsoft Seize 107 Russian Domains in Major Cyber Fraud Crackdown

U.S. and Microsoft Seize 107 Russian Domains in Major Cyber Fraud Crackdown

Phishing attacks armed with AI capabilities are on the rise

Phishing attacks armed with AI capabilities are on the rise

Phishing attacks armed with AI capabilities are on the rise

Phishing attacks armed with AI capabilities are on the rise

New report reveals a rise in phishing attacks, as commodity campaigns, advanced persistent threats, and impersonation attacks escalate

New report reveals a rise in phishing attacks, as commodity campaigns, advanced persistent threats, and impersonation attacks escalate

New report reveals a rise in phishing attacks, as commodity campaigns, advanced persistent threats, and impersonation attacks escalate

New report reveals a rise in phishing attacks, as commodity campaigns, advanced persistent threats, and impersonation attacks escalate
Access Now and Russian civil society victims help take down Russian phishing infrastructure

Access Now and Russian civil society victims help take down Russian phishing infrastructure

Access Now and Russian civil society victims help take down Russian phishing infrastructure

Access Now and Russian civil society victims help take down Russian phishing infrastructure

Businesses are being hit with more mobile phishing than ever before

Businesses are being hit with more mobile phishing than ever before

Businesses are being hit with more mobile phishing than ever before

Businesses are being hit with more mobile phishing than ever before

It's Estimated That 91% Of Cyber Attacks Begin With Phishing Emails

It's Estimated That 91% Of Cyber Attacks Begin With Phishing Emails

It's Estimated That 91% Of Cyber Attacks Begin With Phishing Emails

It's Estimated That 91% Of Cyber Attacks Begin With Phishing Emails

Cybercriminals Exploit HTTP Headers for Credential Theft via Large-Scale Phishing Attacks

Cybercriminals Exploit HTTP Headers for Credential Theft via Large-Scale Phishing Attacks

Cybercriminals Exploit HTTP Headers for Credential Theft via Large-Scale Phishing Attacks

Cybercriminals Exploit HTTP Headers for Credential Theft via Large-Scale Phishing Attacks

Is That Text Message From Your Bank Legit? How to Detect and Avoid SMS Phishing Scams

Is That Text Message From Your Bank Legit? How to Detect and Avoid SMS Phishing Scams

Is That Text Message From Your Bank Legit? How to Detect and Avoid SMS Phishing Scams

Is That Text Message From Your Bank Legit? How to Detect and Avoid SMS Phishing Scams

Honest phishing: the alert is fake, the attack is real

Honest phishing: the alert is fake, the attack is real

Honest phishing: the alert is fake, the attack is real

Honest phishing: the alert is fake, the attack is real
Phishing Remains Top Cyber Threat Despite Drop in Incidents

Phishing Remains Top Cyber Threat Despite Drop in Incidents

Phishing Remains Top Cyber Threat Despite Drop in Incidents

Phishing Remains Top Cyber Threat Despite Drop in Incidents

Google, Facebook and Amazon hit hard by phishing in early 2024

Google, Facebook and Amazon hit hard by phishing in early 2024

Google, Facebook and Amazon hit hard by phishing in early 2024

Google, Facebook and Amazon hit hard by phishing in early 2024

$55 Million in DAI Stolen From This Crypto Whale via Phishing Attack

$55 Million in DAI Stolen From This Crypto Whale via Phishing Attack

$55 Million in DAI Stolen From This Crypto Whale via Phishing Attack

$55 Million in DAI Stolen From This Crypto Whale via Phishing Attack

4014 Phishing links becoming bigger threat than email attachments

4014 Phishing links becoming bigger threat than email attachments

4014 Phishing links becoming bigger threat than email attachments

4014 Phishing links becoming bigger threat than email attachments

4012 University of Toronto - Citizen Lab Rivers of Phish Sophisticated Phishing Targets Russia’s Perceived Enemies Around the Globe/ Access Now Spear-phishing cases from Eastern Europe in 2022-2023 and 2024

4012 University of Toronto - Citizen Lab Rivers of Phish Sophisticated Phishing Targets Russia’s Perceived Enemies Around the Globe/ Access Now Spear-phishing cases from Eastern Europe in 2022-2023 and 2024

4012 University of Toronto - Citizen Lab Rivers of Phish Sophisticated Phishing Targets Russia’s Perceived Enemies Around the Globe/ Access Now Spear-phishing cases from Eastern Europe in 2022-2023 and 2024

4012 University of Toronto - Citizen Lab Rivers of Phish Sophisticated Phishing Targets Russia’s Perceived Enemies Around the Globe/ Access Now Spear-phishing cases from Eastern Europe in 2022-2023 and 2024

Russia launching more sophisticated phishing attacks, new report finds

Russia launching more sophisticated phishing attacks, new report finds

Russia launching more sophisticated phishing attacks, new report finds

Russia launching more sophisticated phishing attacks, new report finds

4010 One of The Biggest Data Breaches Ever Leaks 2.9 Billion Records - Here’s What You Need to Know!

4010 One of The Biggest Data Breaches Ever Leaks 2.9 Billion Records - Here’s What You Need to Know!

4010 One of The Biggest Data Breaches Ever Leaks 2.9 Billion Records - Here’s What You Need to Know!

4010 One of The Biggest Data Breaches Ever Leaks 2.9 Billion Records - Here’s What You Need to Know!

Darktrace report: 56% of phishing emails bypass security checks

Darktrace report: 56% of phishing emails bypass security checks

Darktrace report: 56% of phishing emails bypass security checks

Darktrace report: 56% of phishing emails bypass security checks

The Alarming Surge Of Lateral Phishing – Are We All Just Sitting Ducks?

The Alarming Surge Of Lateral Phishing – Are We All Just Sitting Ducks?

The Alarming Surge Of Lateral Phishing – Are We All Just Sitting Ducks?

The Alarming Surge Of Lateral Phishing – Are We All Just Sitting Ducks?

This Android SMS phishing campaign steals your money AND wipes your data

This Android SMS phishing campaign steals your money AND wipes your data

This Android SMS phishing campaign steals your money AND wipes your data

This Android SMS phishing campaign steals your money AND wipes your data

EchoSpoofing: Lessons Learned from Proofpoint Email Phishing Exploit

EchoSpoofing: Lessons Learned from Proofpoint Email Phishing Exploit

EchoSpoofing: Lessons Learned from Proofpoint Email Phishing Exploit

EchoSpoofing: Lessons Learned from Proofpoint Email Phishing Exploit

Microsoft OneDrive users in India could be tricked into installing a malware this way

Microsoft OneDrive users in India could be tricked into installing a malware this way

Microsoft OneDrive users in India could be tricked into installing a malware this way

Microsoft OneDrive users in India could be tricked into installing a malware this way

Microsoft 365 users targeted by phishers abusing Microsoft Forms

Microsoft 365 users targeted by phishers abusing Microsoft Forms

Microsoft 365 users targeted by phishers abusing Microsoft Forms

Microsoft 365 users targeted by phishers abusing Microsoft Forms

Proofpoint Platform Exploited to Send Millions of Spoofed Phishing Emails

Proofpoint Platform Exploited to Send Millions of Spoofed Phishing Emails

Proofpoint Platform Exploited to Send Millions of Spoofed Phishing Emails

Proofpoint Platform Exploited to Send Millions of Spoofed Phishing Emails

White House Offers Prize Money for Hacker-Thwarting AI

White House Offers Prize Money for Hacker-Thwarting AI

White House Offers Prize Money for Hacker-Thwarting AI

White House Offers Prize Money for Hacker-Thwarting AI

CISA advised individuals to "avoid clicking on phishing emails or suspicious links," as these can lead to email compromises and other scams.

CISA advised individuals to "avoid clicking on phishing emails or suspicious links," as these can lead to email compromises and other scams.

CISA advised individuals to "avoid clicking on phishing emails or suspicious links," as these can lead to email compromises and other scams.

CISA advised individuals to "avoid clicking on phishing emails or suspicious links," as these can lead to email compromises and other scams.

WARNING: Malicious Hackers Exploiting CrowdStrike Outage!

WARNING: Malicious Hackers Exploiting CrowdStrike Outage!

WARNING: Malicious Hackers Exploiting CrowdStrike Outage!

WARNING: Malicious Hackers Exploiting CrowdStrike Outage!

CrowdStrike outage fuels rise in phishing scams, experts argue

CrowdStrike outage fuels rise in phishing scams, experts argue

CrowdStrike outage fuels rise in phishing scams, experts argue

CrowdStrike outage fuels rise in phishing scams, experts argue

Phishing Landscape 2024: An Annual Study of the Scope and Distribution of Phishing

Phishing Landscape 2024: An Annual Study of the Scope and Distribution of Phishing

Phishing Landscape 2024: An Annual Study of the Scope and Distribution of Phishing

Phishing Landscape 2024: An Annual Study of the Scope and Distribution of Phishing

Cybersecurity Funding Jumps 144% In Q2

Cybersecurity Funding Jumps 144% In Q2

Cybersecurity Funding Jumps 144% In Q2

Cybersecurity Funding Jumps 144% In Q2

Google is close to making its biggest acquisition ever

Google is close to making its biggest acquisition ever

Google is close to making its biggest acquisition ever

Google is close to making its biggest acquisition ever

Hack3d: The Web3 Security Quarterly Report - Q2 + H1 2024

Hack3d: The Web3 Security Quarterly Report - Q2 + H1 2024

Hack3d: The Web3 Security Quarterly Report - Q2 + H1 2024

Hack3d: The Web3 Security Quarterly Report - Q2 + H1 2024

Booking.com reports 900% surge in travel scams

Booking.com reports 900% surge in travel scams

Booking.com reports 900% surge in travel scams

Booking.com reports 900% surge in travel scams

A newly discovered security vulnerability allows attackers to impersonate Microsoft corporate email accounts, significantly increasing the risk of phishing attacks.

A newly discovered security vulnerability allows attackers to impersonate Microsoft corporate email accounts, significantly increasing the risk of phishing attacks.

A newly discovered security vulnerability allows attackers to impersonate Microsoft corporate email accounts, significantly increasing the risk of phishing attacks.

A newly discovered security vulnerability allows attackers to impersonate Microsoft corporate email accounts, significantly increasing the risk of phishing attacks.

Phishing attack hits L.A. County public health agency, jeopardizing 200,000-plus residents’ personal info

Phishing attack hits L.A. County public health agency, jeopardizing 200,000-plus residents’ personal info

Phishing attack hits L.A. County public health agency, jeopardizing 200,000-plus residents’ personal info

Phishing attack hits L.A. County public health agency, jeopardizing 200,000-plus residents’ personal info

The Brands and Industries that Phishing Scammers Impersonate the Most

The Brands and Industries that Phishing Scammers Impersonate the Most

The Brands and Industries that Phishing Scammers Impersonate the Most

The Brands and Industries that Phishing Scammers Impersonate the Most

Cybercriminals and AI: Not Just Better Phishing

Cybercriminals and AI: Not Just Better Phishing

Cybercriminals and AI: Not Just Better Phishing

Cybercriminals and AI: Not Just Better Phishing

US, UK, and India lead in phishing attempts in 2023, reports Zscaler ThreatLabz

US, UK, and India lead in phishing attempts in 2023, reports Zscaler ThreatLabz

US, UK, and India lead in phishing attempts in 2023, reports Zscaler ThreatLabz

US, UK, and India lead in phishing attempts in 2023, reports Zscaler ThreatLabz

Phishing scam reports to the Better Business Bureau nearly doubled in 2023

Phishing scam reports to the Better Business Bureau nearly doubled in 2023

Phishing scam reports to the Better Business Bureau nearly doubled in 2023

Phishing scam reports to the Better Business Bureau nearly doubled in 2023

What is spear phishing? Examples, tactics, and techniques

What is spear phishing? Examples, tactics, and techniques

What is spear phishing? Examples, tactics, and techniques

What is spear phishing? Examples, tactics, and techniques

Crypto companies suffer supply chain email breach, users likely to face series of phishing scams

Crypto companies suffer supply chain email breach, users likely to face series of phishing scams

Crypto companies suffer supply chain email breach, users likely to face series of phishing scams

Crypto companies suffer supply chain email breach, users likely to face series of phishing scams

AI Will Increase the Quantity—and Quality—of Phishing Scams

AI Will Increase the Quantity—and Quality—of Phishing Scams

AI Will Increase the Quantity—and Quality—of Phishing Scams

AI Will Increase the Quantity—and Quality—of Phishing Scams

HR & IT emails top phishing attacks, KnowBe4 report reveals

HR & IT emails top phishing attacks, KnowBe4 report reveals

HR & IT emails top phishing attacks, KnowBe4 report reveals

HR & IT emails top phishing attacks, KnowBe4 report reveals

Tech Companies Announce A New Coalition To Fight Online Fraud & Pig Butchering Scams

Tech Companies Announce A New Coalition To Fight Online Fraud & Pig Butchering Scams

Tech Companies Announce A New Coalition To Fight Online Fraud & Pig Butchering Scams

Tech Companies Announce A New Coalition To Fight Online Fraud & Pig Butchering Scams

Report Reveals 341% Rise in Advanced Phishing Attacks

Report Reveals 341% Rise in Advanced Phishing Attacks

Report Reveals 341% Rise in Advanced Phishing Attacks

Report Reveals 341% Rise in Advanced Phishing Attacks

Phishing statistics that will make you think twice before clicking

Phishing statistics that will make you think twice before clicking

Phishing statistics that will make you think twice before clicking

Phishing statistics that will make you think twice before clicking

A Breakdown of Today’s Phishing Epidemic

A Breakdown of Today’s Phishing Epidemic

A Breakdown of Today’s Phishing Epidemic

A Breakdown of Today’s Phishing Epidemic

What is Smishing? SMS phishing explained

What is Smishing? SMS phishing explained

What is Smishing? SMS phishing explained

What is Smishing? SMS phishing explained

Record Number of Mobile Phishing Attacks in 2022

Record Number of Mobile Phishing Attacks in 2022

Record Number of Mobile Phishing Attacks in 2022

Record Number of Mobile Phishing Attacks in 2022

Phishing Scams Growing More Sophisticated, Finra Says

Phishing Scams Growing More Sophisticated, Finra Says

Phishing Scams Growing More Sophisticated, Finra Says

Phishing Scams Growing More Sophisticated, Finra Says

Cybercriminals getting more creative with phishing attacks

Cybercriminals getting more creative with phishing attacks

Cybercriminals getting more creative with phishing attacks

Cybercriminals getting more creative with phishing attacks

Zscaler Report Reveals 50% Annual Surge in Global Phishing Attacks

Zscaler Report Reveals 50% Annual Surge in Global Phishing Attacks

Zscaler Report Reveals 50% Annual Surge in Global Phishing Attacks

Zscaler Report Reveals 50% Annual Surge in Global Phishing Attacks

Phishing FAQ: How to Spot Scams and Stop Them in Their Tracks

Phishing FAQ: How to Spot Scams and Stop Them in Their Tracks

Phishing FAQ: How to Spot Scams and Stop Them in Their Tracks

Phishing FAQ: How to Spot Scams and Stop Them in Their Tracks

Email scams vs Phishing - is there a difference?

Email scams vs Phishing - is there a difference?

Email scams vs Phishing - is there a difference?

Email scams vs Phishing - is there a difference?

UPS discloses data breach after exposed customer info used in SMS phishing

UPS discloses data breach after exposed customer info used in SMS phishing

UPS discloses data breach after exposed customer info used in SMS phishing

UPS discloses data breach after exposed customer info used in SMS phishing

Bored Ape NFTs Worth $135K Stolen by Prolific Phishing Thief

Bored Ape NFTs Worth $135K Stolen by Prolific Phishing Thief

Bored Ape NFTs Worth $135K Stolen by Prolific Phishing Thief

Bored Ape NFTs Worth $135K Stolen by Prolific Phishing Thief

Someone pretended to be Hamilton police — it led to a fake story about cryptocurrency theft

Someone pretended to be Hamilton police — it led to a fake story about cryptocurrency theft

Someone pretended to be Hamilton police — it led to a fake story about cryptocurrency theft

Someone pretended to be Hamilton police — it led to a fake story about cryptocurrency theft

Over $765K worth of NFTs stolen after SIM swap attack on GutterCatGang

Over $765K worth of NFTs stolen after SIM swap attack on GutterCatGang

Over $765K worth of NFTs stolen after SIM swap attack on GutterCatGang

Over $765K worth of NFTs stolen after SIM swap attack on GutterCatGang

Coinbase Users Report Scams and Phishing Attacks on Twitter

Coinbase Users Report Scams and Phishing Attacks on Twitter

Coinbase Users Report Scams and Phishing Attacks on Twitter

Coinbase Users Report Scams and Phishing Attacks on Twitter

Phishing Scam Exposes Vulnerabilities: Man Indicted for Stealing $450,000 in Cryptocurrencies and NFTs

Phishing Scam Exposes Vulnerabilities: Man Indicted for Stealing $450,000 in Cryptocurrencies and NFTs

Phishing Scam Exposes Vulnerabilities: Man Indicted for Stealing $450,000 in Cryptocurrencies and NFTs

Phishing Scam Exposes Vulnerabilities: Man Indicted for Stealing $450,000 in Cryptocurrencies and NFTs

ChatGPT’s evil twin WormGPT is secretly entering emails, raiding banks

ChatGPT’s evil twin WormGPT is secretly entering emails, raiding banks

ChatGPT’s evil twin WormGPT is secretly entering emails, raiding banks

ChatGPT’s evil twin WormGPT is secretly entering emails, raiding banks

Deepfake Imposter Scams Are Driving a New Wave of Fraud

Deepfake Imposter Scams Are Driving a New Wave of Fraud

Deepfake Imposter Scams Are Driving a New Wave of Fraud

Deepfake Imposter Scams Are Driving a New Wave of Fraud

Cybersecurity Experts Warn of Growing Threat Landscape as Phishing Attacks Soar

Cybersecurity Experts Warn of Growing Threat Landscape as Phishing Attacks Soar

Cybersecurity Experts Warn of Growing Threat Landscape as Phishing Attacks Soar

Cybersecurity Experts Warn of Growing Threat Landscape as Phishing Attacks Soar

Phishing Emails Abusing QR Codes Surge

Phishing Emails Abusing QR Codes Surge

Phishing Emails Abusing QR Codes Surge

Phishing Emails Abusing QR Codes Surge

PHISHING GUIDANCE: STOPPING THE ATTACK CYCLE AT PHASE ONE

PHISHING GUIDANCE: STOPPING THE ATTACK CYCLE AT PHASE ONE

PHISHING GUIDANCE: STOPPING THE ATTACK CYCLE AT PHASE ONE

PHISHING GUIDANCE: STOPPING THE ATTACK CYCLE AT PHASE ONE

Cross-Sector Cybersecurity Performance Goals

Cross-Sector Cybersecurity Performance Goals

Cross-Sector Cybersecurity Performance Goals

Cross-Sector Cybersecurity Performance Goals

Cybersecurity Awareness Month Series: Employee Cybersecurity Awareness Training

Cybersecurity Awareness Month Series: Employee Cybersecurity Awareness Training

Cybersecurity Awareness Month Series: Employee Cybersecurity Awareness Training

Cybersecurity Awareness Month Series: Employee Cybersecurity Awareness Training

Crypto wallet Trezor looks into phishing campaign, exec says

Crypto wallet Trezor looks into phishing campaign, exec says

Crypto wallet Trezor looks into phishing campaign, exec says

Crypto wallet Trezor looks into phishing campaign, exec says

LockBit's Disastrous Success + Banks Dragged Kicking and Screaming to Combat Fraud

LockBit's Disastrous Success + Banks Dragged Kicking and Screaming to Combat Fraud

LockBit's Disastrous Success + Banks Dragged Kicking and Screaming to Combat Fraud

LockBit's Disastrous Success + Banks Dragged Kicking and Screaming to Combat Fraud

Latest phishing campaign hits potential Zoom users with malware

Latest phishing campaign hits potential Zoom users with malware

Latest phishing campaign hits potential Zoom users with malware

Latest phishing campaign hits potential Zoom users with malware

Living Off the Land Is the New Normal + When Hacks Upset Housing Markets

Living Off the Land Is the New Normal + When Hacks Upset Housing Markets

Living Off the Land Is the New Normal + When Hacks Upset Housing Markets

Living Off the Land Is the New Normal + When Hacks Upset Housing Markets

Agent Racoon Backdoor Targets Organizations in Middle East, Africa, and U.S.

Agent Racoon Backdoor Targets Organizations in Middle East, Africa, and U.S.

Agent Racoon Backdoor Targets Organizations in Middle East, Africa, and U.S.

Agent Racoon Backdoor Targets Organizations in Middle East, Africa, and U.S.

Threat actors launched a phishing attack against a former employee obtaining his credentials and access to the Ledger’s NPMJS account.

Threat actors launched a phishing attack against a former employee obtaining his credentials and access to the Ledger’s NPMJS account.

Threat actors launched a phishing attack against a former employee obtaining his credentials and access to the Ledger’s NPMJS account.

Threat actors launched a phishing attack against a former employee obtaining his credentials and access to the Ledger’s NPMJS account.

Crypto phishing scams took almost $300M from 324K victims in 2023: Report

Crypto phishing scams took almost $300M from 324K victims in 2023: Report

Crypto phishing scams took almost $300M from 324K victims in 2023: Report

Crypto phishing scams took almost $300M from 324K victims in 2023: Report

Cyber attacks are one of the biggest threats facing healthcare systems

Cyber attacks are one of the biggest threats facing healthcare systems

Cyber attacks are one of the biggest threats facing healthcare systems

Cyber attacks are one of the biggest threats facing healthcare systems

Cybersecurity Trends in Email Protection: What to Watch for in 2024

Cybersecurity Trends in Email Protection: What to Watch for in 2024

Cybersecurity Trends in Email Protection: What to Watch for in 2024

Cybersecurity Trends in Email Protection: What to Watch for in 2024

Financial platform Payoneer blames account hacks on phishing campaign

Financial platform Payoneer blames account hacks on phishing campaign

Financial platform Payoneer blames account hacks on phishing campaign

Financial platform Payoneer blames account hacks on phishing campaign

Coordinated crypto hack and phishing campaign floods investor emails

Coordinated crypto hack and phishing campaign floods investor emails

Coordinated crypto hack and phishing campaign floods investor emails

Coordinated crypto hack and phishing campaign floods investor emails

The Top 11 Phishing Protection Solutions

The Top 11 Phishing Protection Solutions

The Top 11 Phishing Protection Solutions

The Top 11 Phishing Protection Solutions

"Phishing and malicious emails remain the main vectors of infection"

"Phishing and malicious emails remain the main vectors of infection"

"Phishing and malicious emails remain the main vectors of infection"

"Phishing and malicious emails remain the main vectors of infection"

FORBES 101 What Is Phishing? Understanding Cyber Attacks

FORBES 101 What Is Phishing? Understanding Cyber Attacks

FORBES 101 What Is Phishing? Understanding Cyber Attacks

FORBES 101 What Is Phishing? Understanding Cyber Attacks

FCC and crypto firms are being hit in advanced phishing attacks using fake Okta logins

FCC and crypto firms are being hit in advanced phishing attacks using fake Okta logins

FCC and crypto firms are being hit in advanced phishing attacks using fake Okta logins

FCC and crypto firms are being hit in advanced phishing attacks using fake Okta logins

A new version of the most widely-used ransomware today has been spotted — and it's even better at avoiding detection

A new version of the most widely-used ransomware today has been spotted — and it's even better at avoiding detection

A new version of the most widely-used ransomware today has been spotted — and it's even better at avoiding detection

A new version of the most widely-used ransomware today has been spotted — and it's even better at avoiding detection

FBI/IC3 Public Service Announcement Alert Number: I-041224-PSA April 12, 2024

FBI/IC3 Public Service Announcement Alert Number: I-041224-PSA April 12, 2024

FBI/IC3 Public Service Announcement Alert Number: I-041224-PSA April 12, 2024

FBI/IC3 Public Service Announcement Alert Number: I-041224-PSA April 12, 2024
Frequently asked questions
What is the Habit Business Management App, and how does it work?
The Habit Business Management App is a comprehensive tool designed to streamline and enhance various aspects of business operations. It includes features for task management.
How do I get started with the Habit Business Management App?
Is the Habit App suitable for businesses of all sizes?
How does the Habit App encourage team collaboration?
Can I track progress and generate reports using the Habit App?
What is the Habit Business Management App, and how does it work?
The Habit Business Management App is a comprehensive tool designed to streamline and enhance various aspects of business operations. It includes features for task management.
How do I get started with the Habit Business Management App?
Is the Habit App suitable for businesses of all sizes?
How does the Habit App encourage team collaboration?
Can I track progress and generate reports using the Habit App?
What is the Habit Business Management App, and how does it work?
How do I get started with the Habit Business Management App?
Is the Habit App suitable for businesses of all sizes?
How does the Habit App encourage team collaboration?
Can I track progress and generate reports using the Habit App?
What is the Habit Business Management App, and how does it work?
The Habit Business Management App is a comprehensive tool designed to streamline and enhance various aspects of business operations. It includes features for task management.
How do I get started with the Habit Business Management App?
Is the Habit App suitable for businesses of all sizes?
How does the Habit App encourage team collaboration?
Can I track progress and generate reports using the Habit App?
PhishFlagger™ was created to protect consumers and help companies eliminate brand destruction by imposters. We sequentially number outgoing digital communications including Email, Text, SMS and Instant Messaging. This patented protocol will identify threats, keep order in our digital world, making it easier to manage and defend. Consumers will now confidently open emails from trusted senders, maximizing marketing dollars.
Please help spread the word (support/like/comment/join!)
PhishFlagger™
The Email Phishing Solution.
PhishFlagger™ and PhishCounter™ are Trademarks of PhishFlagger Inc. License is required for your Email Numbering solution.
#phishflagger #phishcounter #sendmailsafe #numbering #numberingemail #email #counter #emailnumbering #cybersecurity #emailsecurity #phishing #dataprotection #cyberthreats #informationsecurity #threatintelligence #dataprivacy #digitalsecurity #securityawareness #identityprotection #threatdetection #riskmanagement #securitytraining #infosec #cyberawareness #onlinesafety #databreach #cybersecurityawarenessmonth #itcompliance #compliance #datasecurity #emailphishing #cyberresilience #malware #ransomware #businessemailcompromise #socialengineering
PhishFlagger™ was created to protect consumers and help companies eliminate brand destruction by imposters. We sequentially number outgoing digital communications including Email, Text, SMS and Instant Messaging. This patented protocol will identify threats, keep order in our digital world, making it easier to manage and defend. Consumers will now confidently open emails from trusted senders, maximizing marketing dollars.
Please help spread the word (support/like/comment/join!)
PhishFlagger™
The Email Phishing Solution.
PhishFlagger™ and PhishCounter™ are Trademarks of PhishFlagger Inc. License is required for your Email Numbering solution.
#phishflagger #phishcounter #sendmailsafe #numbering #numberingemail #email #counter #emailnumbering #cybersecurity #emailsecurity #phishing #dataprotection #cyberthreats #informationsecurity #threatintelligence #dataprivacy #digitalsecurity #securityawareness #identityprotection #threatdetection #riskmanagement #securitytraining #infosec #cyberawareness #onlinesafety #databreach #cybersecurityawarenessmonth #itcompliance #compliance #datasecurity #emailphishing #cyberresilience #malware #ransomware #businessemailcompromise #socialengineering
PhishFlagger™ was created to protect consumers and help companies eliminate brand destruction by imposters. We sequentially number outgoing digital communications including Email, Text, SMS and Instant Messaging. This patented protocol will identify threats, keep order in our digital world, making it easier to manage and defend. Consumers will now confidently open emails from trusted senders, maximizing marketing dollars.
Please help spread the word (support/like/comment/join!)
PhishFlagger™
The Email Phishing Solution.
PhishFlagger™ and PhishCounter™ are Trademarks of PhishFlagger Inc. License is required for your Email Numbering solution.
#phishflagger #phishcounter #sendmailsafe #numbering #numberingemail #email #counter #emailnumbering #cybersecurity #emailsecurity #phishing #dataprotection #cyberthreats #informationsecurity #threatintelligence #dataprivacy #digitalsecurity #securityawareness #identityprotection #threatdetection #riskmanagement #securitytraining #infosec #cyberawareness #onlinesafety #databreach #cybersecurityawarenessmonth #itcompliance #compliance #datasecurity #emailphishing #cyberresilience #malware #ransomware #businessemailcompromise #socialengineering
PhishFlagger™ was created to protect consumers and help companies eliminate brand destruction by imposters. We sequentially number outgoing digital communications including Email, Text, SMS and Instant Messaging. This patented protocol will identify threats, keep order in our digital world, making it easier to manage and defend. Consumers will now confidently open emails from trusted senders, maximizing marketing dollars.
Please help spread the word (support/like/comment/join!)
PhishFlagger™
The Email Phishing Solution.
PhishFlagger™ and PhishCounter™ are Trademarks of PhishFlagger Inc. License is required for your Email Numbering solution.
#phishflagger #phishcounter #sendmailsafe #numbering #numberingemail #email #counter #emailnumbering #cybersecurity #emailsecurity #phishing #dataprotection #cyberthreats #informationsecurity #threatintelligence #dataprivacy #digitalsecurity #securityawareness #identityprotection #threatdetection #riskmanagement #securitytraining #infosec #cyberawareness #onlinesafety #databreach #cybersecurityawarenessmonth #itcompliance #compliance #datasecurity #emailphishing #cyberresilience #malware #ransomware #businessemailcompromise #socialengineering
